Information Security vs Cybersecurity In the digital age, where information is the lifeblood of businesses and individuals alike, the terms “information security” and “cybersecurity” are often used interchangeably. However, they represent distinct yet interconnected concepts that play crucial roles in safeguarding data and systems from threats. This article aims to demystify these terms, elucidating their […]
10 Common Pitfalls to Avoid in Information Technology Security Assessments
In today’s digital age, ensuring robust information technology (IT) security is paramount for organizations of all sizes. Conducting regular security assessments is a critical component of an effective cybersecurity strategy. These assessments help identify vulnerabilities, evaluate the effectiveness of security controls, and ensure compliance with regulatory requirements. However, many organizations fall into common pitfalls that […]
5 Key Principles for Designing a Common Data Security Architecture
In today’s interconnected digital world, where data breaches and cyber threats are becoming increasingly common, ensuring the security of sensitive information is a top priority for businesses of all sizes. With the proliferation of data across various systems and platforms, establishing a common data security architecture has become essential. This comprehensive guide explores five key […]
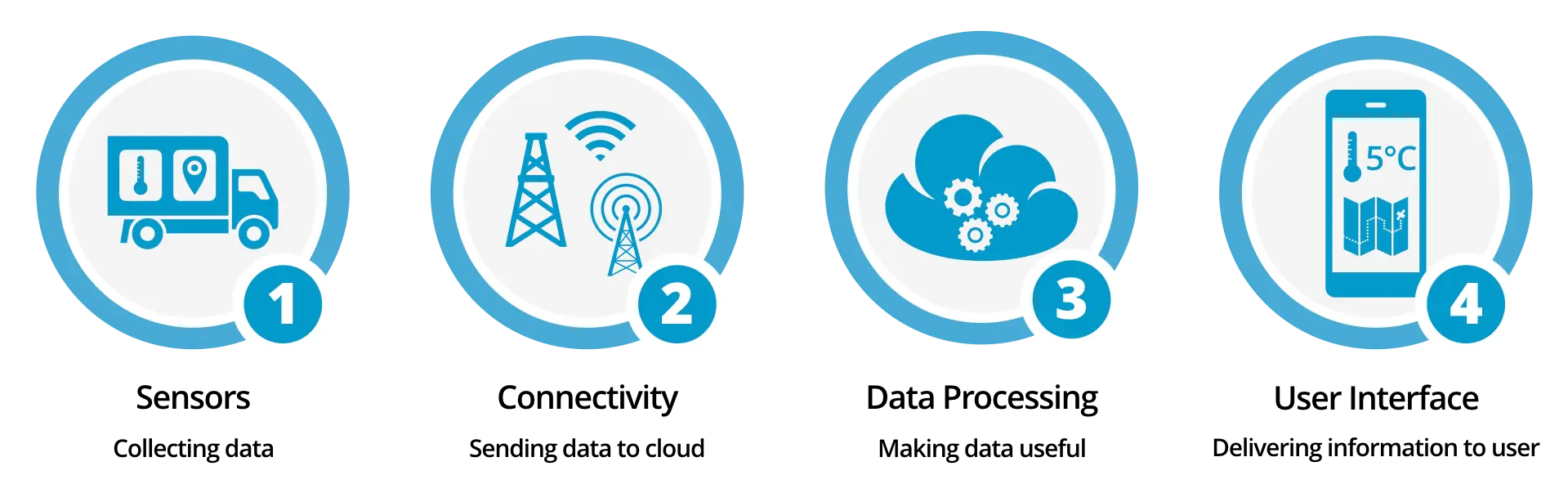
Role of Information Security in Our Dail Life
The Vital Role of Information Security In today’s interconnected world, where the exchange of information is rapid and ubiquitous, the importance of information security cannot be overstated. From personal data to financial transactions, from sensitive corporate information to national security secrets, safeguarding information has become paramount. This article delves into the multifaceted role of information […]
The Role of Artificial Intelligence in Cybersecurity: How AI is Transforming Threat Detection
In the fast-evolving landscape of cybersecurity, traditional methods are increasingly proving insufficient to combat sophisticated cyber threats. Enter Artificial Intelligence (AI), a game-changer in the realm of cybersecurity. AI’s ability to analyze vast amounts of data, learn from patterns, and make decisions in real-time is revolutionizing threat detection and response. This article delves into the […]
Why Zero Trust Architecture is the Future of Enterprise Information Security
In today’s hyperconnected digital landscape, where cyber threats continue to evolve in sophistication and frequency, traditional security approaches are no longer sufficient to protect sensitive data and assets. As organizations grapple with the challenges of securing their increasingly complex IT environments, a paradigm shift towards Zero Trust Architecture (ZTA) is gaining momentum. In this comprehensive […]
Why Zero Trust Architecture is Essential for Modern Cybersecurity
In an era where cyber threats are becoming increasingly sophisticated, traditional cybersecurity models are proving inadequate. Enter Zero Trust Architecture (ZTA), a paradigm shift that is rapidly gaining traction among cybersecurity professionals and organizations. Unlike traditional security models that rely on perimeter defenses, Zero Trust operates on the principle of “never trust, always verify.” This […]
How to Build a Scalable Enterprise Information Security Architecture for Cloud Environments
In the era of cloud computing, where businesses increasingly rely on cloud services to store, process, and manage their data, building a scalable enterprise information security architecture is essential for protecting sensitive information from cyber threats. This comprehensive guide will walk you through the step-by-step process of building a robust and scalable security architecture tailored […]
5 Ways to Enhance Employee Training for Cybersecurity
In today’s digital age, cybersecurity has become a critical concern for businesses of all sizes. With cyber threats evolving and becoming increasingly sophisticated, it’s essential for organizations to ensure their employees are well-trained in cybersecurity practices. Enhancing employee training for cybersecurity can help protect sensitive data, maintain customer trust, and avoid costly breaches. Here are […]
5 Key Components of an Effective Enterprise Information Security Architecture
In today’s digital age, where information is the lifeblood of businesses, protecting it from cyber threats is of paramount importance. An effective enterprise information security architecture serves as the bedrock for safeguarding sensitive data, maintaining operational integrity, and preserving customer trust. In this comprehensive guide, we’ll explore the essential components that constitute a robust enterprise […]